SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension15 GA
This document provides guidance and an overview to high level general features and updates for SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA. Besides product-specific information, it also describes the capabilities and limitations of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA.
These release notes are updated periodically. The latest version of these release notes is always available at https://www.suse.com/releasenotes. General documentation can be found at https://www.suse.com/documentation/sled-15.
These release notes are updated periodically. The latest version of these release notes is always available at. 2.3.1 System Roles for SUSE Linux Enterprise Desktop # With SLED 15, it is possible to choose specific roles for the system based on modules selected during the installation process. Autocrypt: Automatically generates. Aug 11, 2018 AutoCrypt 2.3.1 is just $5.99 USD (or an equivalent amount in other currencies) and is available worldwide through the Mac App Store in the Productivity category. Jul 11, 2018 AutoCrypt works basing its actions on simplicity and is the ideal solution to be used as a batch mode encryptor and decryptor, but can also be used as a standard encryption tool. AutoCrypt uses the latest technology with asynchronous tasks to perform fast and fluid encryption and decryption.
- 1 About the Release Notes
- 2 SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension
- 2.1 Interoperability and Hardware Support
- 2.2 Support and Life Cycle
- 2.3 What Is New?
- 2.4 Documentation and Other Information
- 2.5 Support Statement for SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension
- 2.6 General Support Statement
- 2.7 Technology Previews
- 2.8 Related Products
- 3 Installation and Upgrade
- 3.1 Installation
- 3.2 Update-Related Notes
- 4 Kernel
- 4.1 Support for Scalable Machine Check Architecture (Scalable MCA)
- 4.2 Support for AMD Memory Encryption
- 5 Kernel Modules
- 5.1 Using Thunderbolt Devices
- 6 Systems Management
- 6.1 Support for Socket-Based Services Activation
- 7 Storage
- 7.1 Updated Btrfs Subvolume Layout
- 8 Security
- 8.1 GPG Does Not Support GPG V3 Keys Anymore, Resulting in Zypper/rpm Warnings
- 8.2 GnuPG Uses SHA-2 Family of Digests by Default
- 8.3 All SLE 15 Packages Are Enabled for Address Space Layout Randomization
- 8.4 firewalld Replaces SuSEfirewall2 as Default Software Firewall
- 9 Networking
- 9.1 Mozilla Thunderbird Provided as a Cross-Platform E-Mail Client
- 9.2 Enigmail Extension Provided for OpenPGP Support in Mozilla Thunderbird
- 10 Virtualization
- 10.1 Support for Nested Virtualization Performance Features in Newer AMD Processors
- 11 Miscellaneous
- 11.1 Plymouth/GDM May Hang If No Display Is Connected
- 11.2 Graphics Chipset Compatibility under Wayland
- 11.3 No Default Compose Key Combination
- 11.4 Wayland Cannot Be Used on Machines with Hybrid GPUs
- 12 Packages and Functionality Changes
- 12.1 New Packages
- 12.2 Updated Packages
- 12.3 Removed Packages and Features
- 12.4 Modules
- 13 Obtaining Source Code
- 14 Legal Notices
The most recent version of these Release Notes is always available online at https://www.suse.com/releasenotes.
Some entries may be listed twice, if they are important and belong to more than one section.
Release notes usually only list changes that happened between two subsequent releases. Always review all release notes documents that apply in your upgrade scenario.
2 SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension#
SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension is the market's only enterprise-quality Linux desktop ready for routine business use. Developed and backed by SUSE, SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension provides market-leading usability, seamless interoperability with existing IT systems, and dozens of essential applications—all at a fraction of the price of proprietary operating systems.
It comes bundled with the latest versions of leading applications such as LibreOffice office productivity suite, Mozilla Firefox Web browser, and Evolution e-mail and calendar suite. In addition, it integrates with Microsoft SharePoint for group collaboration and supports a wide range of multimedia file formats, wireless and networking standards, and plug-and-play devices.
Through the latest enhancements in power management and security, SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension also provides an environmentally friendly IT experience (Green IT) and an error-proof desktop. Finally, SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension offers unparalleled flexibility. You can deploy it on a wide range of thick client devices (including desktops, notebooks, netbooks, and workstations), on thin client devices, or as a virtual desktop. By leveraging the power of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension, your business can dramatically reduce costs, improve end user security and increase workforce productivity.
SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 has a 10 year life cycle. The current version (GA) will be fully maintained and supported until 6 months after the release of SUSE Linux Enterprise 15 SP1.
SUSE does not support skipping Service Packs of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension when upgrading.
SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 introduces many innovative changes compared to SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 12.
2.3.1 System Roles for SUSE Linux Enterprise Desktop#
With SLED 15, it is possible to choose specific roles for the system based on modules selected during the installation process. There are four roles available:
GNOME Desktop (Wayland): available when Desktop Productivity (on SLED) or Workstation Extension are selected.
GNOME Desktop (X11): available when Desktop Productivity (on SLED) or Workstation Extension are selected.
GNOME Desktop (Basic): available when the Desktop Application module is selected.
IceWM Desktop (Minimal): available when Basesystem module is selected.
Read the READMEs on the media.
Get the detailed changelog information about a particular package from the RPM (FILENAME is the name of the RPM):
Check the
ChangeLogfile in the top level of the media for a chronological log of all changes made to the updated packages.Find more information in the
docudirectory of the media of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA.
Autocrypt 2.3.1 Crack
For the most up-to-date version of the documentation for SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA, see https://www.suse.com/documentation/sled-15.
2.5 Support Statement for SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension#
To receive support, you need an appropriate subscription with SUSE. For more information, see https://www.suse.com/support/programs/subscriptions/?id=SUSE_Linux_Enterprise_Server.
XFS reflink support is currently considered experimental in current upstream Linux and is also not supported in SUSE Linux Enterprise.
Technology previews are packages, stacks, or features delivered by SUSE. These features are not supported. They may be functionally incomplete, unstable or in other ways not suitable for production use. They are mainly included for customer convenience and give customers a chance to test new technologies within an enterprise environment.
Autocrypt 2.3.1 For Anet
Technology previews can be dropped at any time and SUSE does not commit to providing a supported version of such technologies in the future.
Give your SUSE representative feedback, including your experience and use case.
2.7.1 Support for AMD Secure Encrypted Virtualization#
As a technology preview, SLE 15 now supports AMD Secure Encrypted Virtualization (SEV). SEV integrates main memory encryption capabilities (SME) with the existing AMD-V virtualization architecture to support encrypted virtual machines. Encrypting virtual machines helps protect them from physical threats and other virtual machines or even the hypervisor itself. SEV represents a new approach to security that is particularly suited to cloud computing where virtual machines may not fully trust the hypervisor and administrator of their host system. As with SME, no application software modifications are required to support SEV.
See also Section 4.2, “Support for AMD Memory Encryption” .
This section lists related products. Usually, these products have own release notes documents that are available from https://www.suse.com/releasenotes.
SUSE Enterprise Storage: https://www.suse.com/products/suse-enterprise-storage
SUSE Linux Enterprise Server: https://www.suse.com/products/server
SUSE Linux Enterprise Server for SAP Applications: https://www.suse.com/products/sles-for-sap
SUSE Manager: https://www.suse.com/products/suse-manager
SUSE OpenStack Cloud: https://www.suse.com/products/suse-openstack-cloud
Additionally, there is the following extension which is not covered by SUSE support agreements, available at no additional cost and without an extra registration key:
This section includes information related to the initial installation of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA. For installation documentation, see Deployment Guide at https://www.suse.com/documentation/sled-15/singlehtml/book_sle_deployment/book_sle_deployment.html.
This section includes information related to the initial installation of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA.
Important: Installation Documentation
The following release notes contain additional notes regarding the installation of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension. However, they do not document the installation procedure itself.
For installation documentation, see Deployment Guide at https://www.suse.com/documentation/sled-15/singlehtml/book_sle_deployment/book_sle_deployment.html.
3.1.1 Parted Supports Linux-Specific GPT GUID for Partitions#
When Parted 3.1, the version shipped with earlier versions of SLE, was released, there was no Linux-specific GPT GUID. Therefore, it used the Microsoft Basic Data partition type for all new partitions.
With SLE 15, Parted 3.2 is shipped. This version uses the new Linux GPT GUID by default. If an old Linux GPT partition that uses the Microsoft Basic Data type is found, Parted will set the flag msftdata on it.
In partition editors and other GPT-enabled disk tools, such partitions may be mislabeled as Windows Data Partitions or similar. This affects the YaST Expert Partitioner, as well as fdisk, gdisk, etc.
The partition can be converted and the flag be cleared like this:
On SLED 15, users of Nvidia graphical chipsets can choose between two different drivers:
The proprietary Nvidia driver, which is available after registering at the SUSE Customer Center from the repository
SUSE_Linux_Enterprise_Desktop_15_x86_64:SLE-15-GA-Desktop-nVidia-Driver. This driver is fully supported by Nvidia.The Nouveau driver (available in the
kernel-default-extraandxf86-video-nouveaupackages), which is provided as-is and not supported by SUSE.
Installing the proprietary Nvidia driver will disable the nouveau driver.
This section includes upgrade-related information for SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension 15 GA.
Important: Upgrade Documentation
The following release notes contain additional notes regarding the upgrade of SUSE Linux Enterprise Desktop/SUSE Linux Enterprise Workstation Extension. However, they do not document the upgrade procedure itself.
For upgrade documentation, see https://www.suse.com/documentation/sled-15/singlehtml/book_sle_deployment/book_sle_deployment.html#cha.update.sle.
3.2.1 The User Space X Drivers cirrus/mga/ast Have Been Removed#
The packages xf86-video-cirrus, xf86-video-mga, and xf86-video-ast have been removed in SLE 15. Kernel mode setting and mode-setting X drivers for these graphics cards have been available throughout the SLE 12 cycle and were used for all new SLE 12 installations. The user space X driver packages were only retained to ease upgrades from SLE 11.
If you are upgrading a machine from SLE 12 to SLE 15 that has previously been upgraded from SLE 11 to SLE 12, X may no longer start after the upgrade to SLE 15. If that is the case, rename or remove the file /etc/X11/xorg.conf, for example using:
ReiserFS support for new installations was removed from YaST in SUSE Linux Enterprise 12 but upgrades were still supported.
With SUSE Linux Enterprise 15, support for ReiserFS will be completely removed from YaST and the installer will block the upgrade when it detects a ReiserFS file system.
For existing data partitions formatted with ReiserFS, we suggest converting them to Btrfs before migrating your system to SUSE Linux Enterprise 15.
3.2.3 System-wide Locale/Keymap/Font Settings are not read from /etc/sysconfig/ anymore#
Previously, there were different places for configuring a given setting.
For example, to set the system-wide locale, you could either:
write the settings in
/etc/locale.confuse
localectlwrite
ROOT_USES_LANGin/etc/sysconfig/languageifLANGwas not already configured in/etc/locale.conf.
This could be confusing, especially since settings in /etc/sysconfig/language usually override the locale settings used by users's shells only and therefore should not influence the system-wide locale.
Similar situations and similar problems could also be seen for the keymap/font settings:
The keyboard layout could be configured in both
/etc/vconsole.confand/etc/sysconfig/keyboard, the former having a higher priority.the font used by virtual consoles could be read from both
/etc/vconsole.confand/etc/sysconfig/console.conf, the former having a higher priority.
With SLE 15, systemd does not read certain settings from the following files anymore:
/etc/sysconfig/languagefor the system-wide locale settings (ROOT_USES_LANG)/etc/sysconfig/keyboardfor the keyboard layout used by the virtual consoles (CONSOLE_FONT,CONSOLE_SCREENMAP,CONSOLE_UNICODEMAP)/etc/sysconfig/consolefor the font used by the virtual consoles (KEYTABLE)
All variables defined in /etc/sysconfig/language will still be used to override the system-wide locale and to define a different locale settings for users's shells as it is currently described in the official documentation.
To keep backward compatibility with the old systems, during the update of the systemd package, all variables mentioned will be migrated from sysconfig to their final destinations if they are not already defined there.
Locale:
The system-wide locale can be changed via
localectl(1)or YaST.The settings are stored in
/etc/locale.conf, seeman 5 locale.conf.
Virtual Consoles: The settings can instead be written directly in /etc/vconsole.conf. Also see man 5 vconsole.conf.
Keyboard:
The system-wide locale can be changed via localect(1).
The settings are stored in /etc/vconsole.conf, see man vconsole.conf(5).
4.1 Support for Scalable Machine Check Architecture (Scalable MCA)#
Scalable MCA improves hardware error reporting to better diagnose issues in AMD Zen processors. It provides a clearer, easier to use rules for the kinds of information supplied by the hardware when reporting errors.
This clearer separation of architectural and implementation-specific functions allows operating systems to better take advantage of architectural features.
In addition, it expands information logged in MCA banks to allow for improved error handling, better diagnosability, and future scalability.
To provide protection against physical attacks on a system, AMD SME can provide full or partial memory encryption depending on the use case, on AMD family 17h CPU processors. Full memory encryption means all DRAM contents are encrypted using random keys. This provides strong protection against cold boot, DRAM interface snooping and similar types of attacks. This technology is especially prominent for systems equipped with NVDIMMs whose contents remain intact after powering down the system.
Memory encryption support is present in SLE 15 kernels but not enabled by default. To enable it on compatible hardware (AMD family 17h CPU, with proper BIOS/UEFI support), supply the boot option mem_encrypt=on.
An important requirement for every Enterprise operating system is the level of support customer receive for their environment. Kernel modules are the most relevant connector between hardware (“controllers”) and the operating system.
For more information about the handling of kernel modules, see the SUSE Linux Enterprise Administration Guide.
SLE 15 supports the Thunderbolt hardware interface. However, there are limitations to this support:
Hot-unplugging is supported on a bus level but we cannot guarantee that every PCI driver also used for Thunderbolt devices supports it.
GPUs must not be hotplugged/hot-unplugged, as doing so can crash the system.
Thunderbolt monitors are not supported.
Systemd allows for new ways of starting services, such as the so-called socket-based activation. Services which are configured to be started on demand will not run until it is needed, for example, when a new request comes in.
The YaST Services Manager has been extended to allow setting services to be started on-demand. Currently, only a subset of services supports this configuration. The current start mode is displayed in the column Start of the YaST Services Manager. In the drop-down box Start Mode of the YaST Services Manager, the mode On-demand will only be shown when it is available for the selected service.
Additionally, the table column Active has been adapted to show the correct value provided by Systemd.
SLE 15 introduces a new default Btrfs subvolume layout that aims for the following:
Simplified snapshots and rollbacks
Prevention of accidental data loss
Better performance of databases and VM images stored in
/var
Instead of using multiple Btrfs subvolumes for different subdirectories of /var, SLE 15 ships with a single subvolume for all of /var. This new subvolume has copy-on-write functionality disabled.
There is no defined way of upgrading to this new Btrfs subvolume layout. Therefore, if you want to take advantage of it, make sure to freshly install SLE 15 instead of upgrading.
For more information on the default Btrfs subvolume layout before and after this change, see https://en.opensuse.org/SDB:BTRFS.
8.1 GPG Does Not Support GPG V3 Keys Anymore, Resulting in Zypper/rpm Warnings#
SLE 12 shipped with GPG 2.0, while SLE 15 includes GPG 2.2. In between these GPG versions, support for GPG V3 keys was removed. If your system's key database still contains GPG V3 keys, you may receive warnings about this when executing Zypper or rpm commands, as these commands are checking the integrity of the package database. These warnings take the form warning: Unsupported version of key: V3.
Usually, these warnings are benign, as these keys may have been used for repositories that are no longer enabled on the system or that have since had key updates. However, if these keys are still in active use by the upstream repository, they must be replaced as soon as possible:
Package management tools in SLE 15 can no longer use them to verify package integrity.
The keys in themselves are insecure. Hence, even though older package management tools will use them to verify integrity of packages, the result of this check cannot be trusted anymore.
To delete such keys, perform the following:
Run an
rpmtt with high verbosity and check its output:In the example, header 168 is associated with an outdated key - the warning appears directly after the message that this specific header is being checked.
Find out the key number associated with the header:
rpm -q --querybynumber HEADERReplace
HEADERwith the required header number. In the example, that would be168.This command returns a key identifier starting with
gpg-pubkey-.(Optional) Use the key identifier (
KEY_ID) to learn more about the key:rpm -qi KEY_IDRemove the key from the system:
sudo rpm -e KEY_IDIf you continue to see warnings on subsequent uses of package management tools, repeat the procedure.
8.2 GnuPG Uses SHA-2 Family of Digests by Default#
Research was published that showed weakesses in the SHA-1 family of hashes for some applications. The use of stronger digests is advised for most applications.
The default behavior for GnuPG (gpg2) has been changed to use SHA-2 family digests for key certificates, default preferences stored in keys, and signature generation in the absense of a configuration file. GnuPG no longer generates a new configuration when called in an empty home. Existing GnuPG configurations are not altered. GnuPG continues to support SHA-1 digest generation and verification as mandated by OpenPGP standards.
8.3 All SLE 15 Packages Are Enabled for Address Space Layout Randomization#
Security consists of layers of defense. One of those layers of defense is randomizing address for programs, so offsets and functions and similar are at randomized addresses on every start.
All SUSE Linux Enterprise 15 binaries are built with support for PIE (Position-Independent Executables) which will randomize all code layout in memory on every startup of the binary.
8.4 firewalld Replaces SuSEfirewall2 as Default Software Firewall#
SuSEfirewall2 was originally tailored towards running a router with forwarding and/or NAT rules. This use case is rarely required anymore. Furthermore, the static nature of SuSEfirewall2 made it difficult to react to today's dynamic networking events like hotplugged network interfaces or virtual networking.
To allow greater flexibility in SLE 15, the default firewall has been switched to the firewalld upstream solution. It provides a resident daemon process which can dynamically adjust firewall rules on behalf of the user or other programs. SuSEfirewall2 is no longer available.
There is no automatic migration from SuSEfirewall2 to firewalld. To migrate an existing SuSEfirewall2 configuration to firewalld, you can use the script from the package susefirewall2-to-firewalld. However, after running the script, you still need to manually adjust and verify the resulting firewalld rules.
More technical information about firewalld could be found in the Security Guide at https://www.suse.com/documentation/sles-15/singlehtml/book_security/book_security.html#sec.security.firewall.firewalld.
9.1 Mozilla Thunderbird Provided as a Cross-Platform E-Mail Client#
Mozilla Thunderbird is provided as a cross-platform graphical e-mail client with calendaring capabilities. It supports the S/MIME (RFC 2633) e-mail encryption standard. Support for OpenPGP (RFC 2440) can be added by installing the extension Enigmail (package enigmail).
9.2 Enigmail Extension Provided for OpenPGP Support in Mozilla Thunderbird#
Mozilla Thunderbird provides support for the S/MIME (RFC 2633) e-mail encryption standard, but needs and additional plugin-in to support OpenPGP (RFC 2440).
The Enigmail plugin for Mozilla Thunderbird is provided to add support for OpenPGP (RFC 2440) e-mail encryption. It uses the local GnuPG installation, configuration and keys.
Additionally, the plugin adds support for the following protocols, enabled by default:
Protected e-mail headers: Encrypts e-mail subjects and replaces them with a dummy text.
Autocrypt: Automatically generates and exchanges encryption keys to seamlessly switch to encrypted communication without user configuration.
Web Key Discovery: Discovers and downloads unavailable keys during message composition.
Pretty Easy Privacy: Scheme for end-to-end e-mail encryption.
10.1 Support for Nested Virtualization Performance Features in Newer AMD Processors#
In nested virtualization, the hypervisor has to intercept and emulate most virtualization instructions in KVM guests in software. This slows down nested virtualization.
Newer AMD processors have support for hardware virtualization of common virtualization instructions, making software emulation unnecessary. These features in newer AMD processors are now supported, making nested virtualization faster.

11.1 Plymouth/GDM May Hang If No Display Is Connected#
When you are using the graphical boot target (with GDM) but there is no display connected, Plymouth may be unable to quit. This affects the start of systemd services that are normally started subsequent to Plymouth.
To diagnose whether a system is in the problematic status, remotely log in to it and run the command systemctl list-jobs. The system is affected if the plymouth-quit-wait.service is shown as running.
Any of the following methods can be used as a workaround:
Connect the machine to a monitor.
Add
plymouth.enable=0in kernel boot options.Run command
plymouth quitwhen the system is running to the status.
11.2 Graphics Chipset Compatibility under Wayland#
The drivers for the following graphics chipsets do not yet support Wayland sessions:
Nvidia GPUs running under the proprietary driver from Nvidia
Cirrus Logic chipsets in QEMU virtual machines
Matrox mgag20 chipset
Aspeed graphics chipsets
In all of these cases, even if the Wayland stack is fully installed, GNOME will automatically fall back to starting an X session.
In previous versions of SLE, the compose key combination allowed typing characters that were not part of the regular keyboard layout. For example, to produce 'å', you could press and release Shift-Right Ctrl and then press a twice.
Starting with SLE 15, there is no longer a predefined compose key combination because Shift-Right Ctrl does not work as expected anymore.
To define a system-wide custom compose key combination, use the file
/etc/X11/Xmodmapand look for the following lines:To uncomment the example code, remove the
!characters at the beginning of lines. However, note that the setup fromXmodmapwill be overwritten if you are usingsetxkbmap.To define a user-specific compose key combination, use your desktop's keyboard configuration tool or the command-line tool
setxkbmap:For the variable
COMPOSE_KEY, use your preferred character, for exampleralt,lwin,rwin,menu,rctl, orcaps.Alternatively, use an IBus input method that allows typing the characters you need without a Compose key.
11.4 Wayland Cannot Be Used on Machines with Hybrid GPUs#
On SLED 15, hybrid GPUs are not fully supported on Wayland. This affects, for example, laptops that have an integrated Intel GPU and a discrete Nvidia or AMD GPU connected to the HDMI ports. When the BIOS of a machine is set to use discrete graphics, GNOME will automatically fall back to starting an X session (which better supports the discrete GPU).
There is an unsupported workaround to use Wayland when a discrete graphic card is enabled. This workaround brings up GNOME on Wayland under SLED 15. However, external monitors with discrete graphic cards are not allowed in this configuration and it can lead to additional display-related issues.
To enable the unsupported workaround, do:
Append the following line to the file
/etc/environment:
wodim was created as fork of cdrtools. Unfortunately, the wodim project stagnated over the years.
SLE 15 migrates back to using cdrtools. This means that some tools have been renamed. The following package names have changed:
genisoimagehas been renamed tomkisofswodimhas been renamed tocdrecordicedaxhas been renamed tocdda2wav
cdrkit-cdrtools-compat is no longer supplied. It only provided symbolic links for compatibility between cdrtools and wodim. If you were using it, no changes are necessary. If you were using the replaced packages above, executable binaries were renamed accordingly.
UnRAR is freeware command-line application for extracting RAR archives. Unfortunately, it is non-free.
In SLE 15, The Unarchiver command-line tool, which is LGPL-licensed (package unar, binaries unar and lsar), has replaced UnRAR.
Unarchiver supports the same archive formats (including RAR5), except for UUE, JAR, and limited support for ARJ (no multi-part) and ACE (no support for Ace 2.0).
UnRAR and Unarchiver are not completely CLI-compatible, as they have a different set of options. Because of this, a simple wrapper script was added within the unrar_wrapper package (with a symbolic link to /usr/bin/unrar). This script transforms a subset of unrar commands to unar and lsar to provide a backwards compatibility:
Supported commands:
l[t[a],b],t,v[t[a],b],x.Supported options:
-o+,-o-,-or,-pOther:
files,@listfilesandpath_to_extract/(only for extracting)Return codes:
0(success),1(error),2(invalid argument)
For more information about functionality supported by the wrapper, see https://github.com/openSUSE/unrar_wrapper.
The time server synchronization daemon ntpd has been replaced with the more modern daemon Chrony.
This change means that AutoYaST files with an ntp_client section need to be updated to a new format for this section. For more information about the new AutoYaST ntp_client format, see AutoYaST Guide, section NTP Client (https://www.suse.com/documentation/sles-15/singlehtml/book_autoyast/book_autoyast.html#Configuration.Network.Ntp).
To sync time in intervals, YaST sets up a cron configuration file. From SLE 15 on, the configuration file used for this is owned by the package yast2-ntp-client (previously no package owned it). The configuration file has been renamed from novell.ntp-synchronization to suse-ntp_synchronization to be consistent with other cron configuration files. The upgrade from ntpd to Chrony is performed automatically during the SLE upgrade: If a file with the old name is found, it will be renamed and references to ntpd in it will be replaced by chrony.
ntpd has been moved to the Legacy module. For more information, see Section 12.4.1, “Legacy Module: ntpd is now part of the Legacy Module”.
12.2.1 Wireshark Qt UI Replaces Deprecated GTK+ UI#
The GTK+ user interface of the Wireshark network protocol analyzer has been deprecated by the upstream project.
The Wireshark Qt interface is now shipped in the package wireshark-ui-qt.
GCC 7.4 and GCC 8.2
glibc 2.26
Linux kernel 4.12
GNOME 3.26
X.org 7.6
Samba 4.7
UEFI Enablement on AMD64/Intel 64
SWAP over NFS
Python 2.7 and Python 3.6
Perl 5.26
Ruby 2.5
The following packages have been removed in this release.
12.3.1 The User Space X Drivers cirrus/mga/ast Have Been Removed#
The packages xf86-video-cirrus, xf86-video-mga, and xf86-video-ast have been removed in SLE 15. Kernel mode setting and mode-setting X drivers for these graphics cards have been available throughout the SLE 12 cycle and were used for all new SLE 12 installations. The user space X driver packages were only retained to ease upgrades from SLE 11.
If you are upgrading a machine from SLE 12 to SLE 15 that has previously been upgraded from SLE 11 to SLE 12, X may no longer start after the upgrade to SLE 15. If that is the case, rename or remove the file /etc/X11/xorg.conf, for example using:
In SLE 15, the package x11vnc is not available anymore. Instead, use x0vncserver. The command x11vnc is now a compatibility wrapper that internally starts x0vncserver. It does not have all features that x11vnc had, but it is faster, more secure, and built from better tested and maintained code.
This section contains information about important changes to modules.
12.4.1 Legacy Module: ntpd is now part of the Legacy Module#
With SLE 15, the network time daemon ntpd has been replaced by chrony. ntpd has been moved to the Legacy module instead.
12.4.2 Legacy Module: OpenSSL 1.0.x Has Been Moved to the Legacy Module#
The lifetime of OpenSSL versions 1.0.x does not cover the full lifetime of the product. Additionally, OpenSSL will not support TLS 1.3. However, some applications may require this older version for a transitional period.
OpenSSL libraries version 1.0.x were moved to the Legacy Module. The module has a different lifecycle from SUSE Linux Enterprise Server itself. This version is not expected to receive feature updates or security certifications. For new development, make sure to use the default OpenSSL version 1.1.x.
This SUSE product includes materials licensed to SUSE under the GNU General Public License (GPL). The GPL requires SUSE to provide the source code that corresponds to the GPL-licensed material. The source code is available for download at http://www.suse.com/download-linux/source-code.html. Also, for up to three years after distribution of the SUSE product, upon request, SUSE will mail a copy of the source code. Requests should be sent by e-mail to mailto:sle_source_request@suse.com or as otherwise instructed at http://www.suse.com/download-linux/source-code.html. SUSE may charge a reasonable fee to recover distribution costs.
SUSE makes no representations or warranties with regard to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, SUSE reserves the right to revise this publication and to make changes to its content, at any time, without the obligation to notify any person or entity of such revisions or changes.
Further, SUSE makes no representations or warranties with regard to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, SUSE reserves the right to make changes to any and all parts of SUSE software, at any time, without any obligation to notify any person or entity of such changes.
Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classifications to export, re-export, or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical/biological weaponry end uses. Refer to https://www.suse.com/company/legal/ for more information on exporting SUSE software. SUSE assumes no responsibility for your failure to obtain any necessary export approvals.
Copyright © 2010-2019 SUSE LLC. This release notes document is licensed under a Creative Commons Attribution-NoDerivs 3.0 United States License (CC-BY-ND-3.0 US, https://creativecommons.org/licenses/by-nd/3.0/us/).
SUSE has intellectual property rights relating to technology embodied in the product that is described in this document. In particular, and without limitation, these intellectual property rights may include one or more of the U.S. patents listed at https://www.suse.com/company/legal/ and one or more additional patents or pending patent applications in the U.S. and other countries.
For SUSE trademarks, see SUSE Trademark and Service Mark list (https://www.suse.com/company/legal/). All third-party trademarks are the property of their respective owners.
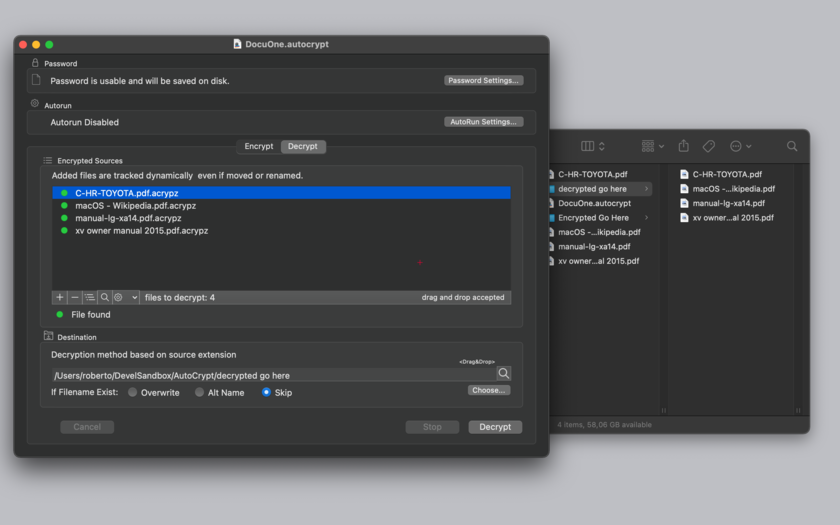
AutoCrypt 2.3.1
Description
AutoCrypt, is an encryption/decryption app with a unique approach.
Using a document based application, AutoCrypt lets the user save in a document all the settings used to encrypt files using AES-256 encryption algorithm
Using these documents, AutoCrypt can be used for encryption and decryption batch process of large quantity of files.
With AutoCrypt, a single click is enough to encrypt hundred of files to a destination place.
Using the powerful AES-256 algorithm provided by Apple CommonCrypt, all the encrypted files will be totally unreadable by anyone, except who knows the correct password.
The obtained encrypted files can be transmitted or stored in unsafe places (as example internet servers) without any security problem (any internet server is an unsafe place by definition)
All the setting used to encrypt the original files, are saved inside an AutoCrypt document.
In few words an AutoCrypt document is a collection of setting used to encrypt or decrypt a collection of files.
In case the files to encrypt or to decrypt are updated with frequencies, an AutoCrypt document, listing this files, provides a one click method to frequently encrypt them storing the updated files in a standard place, even using unattended operation.
The user can also launch AutoCrypt in the night using a document with the ‘Autorun’ option turned on.
AutoCrypt works basing its actions on simplicity and is the ideal solution to be used as a batch mode encryptor and decryptor, but can also be used as a standard encryption tool.
AutoCrypt uses the latest technology with asynchronous tasks to perform fast and fluid encryption and decryption
All the details of the job AutoCrypt has to perform is stored inside AutoCrypt documents (.autocrypt)
When AutoCrypt performs its job, it processes a list of files, one by one, reads each one, encrypts it and saves it in another location appending a .acrypt or .acrypx or .acrypz to the name
AutoCrypt can also automatize the reversed process, decrypting files to plain files and saving them in another place removing the .acrypt , .acripx, .acrypz at the end of the name
AutoCrypt uses the latest Apple technology:
– Sandbox: The app works at the maximum security level
– Resume: the app will reopen at the point and state the user left it
– Auto save: the app saves using the macOS autosave functionality
– Versions: the user can look at previous versions of documents and restore to any earlier version
– Full Screen: the user can switch at any time to full screen using the native macOS full screen mode and commands
– Asynchronous tasks
Features:
– Can work as a desktop tool or as a batch utility
– Save inside documents all the setting used to encrypt and decrypt group of files
– Encrypt and save in a custom place with one click or even unattended
– Can encrypt and decrypt using the same document
– Accept input via drag and drops for an immediate and easy input
– Its fast and effective using multithreading technology
– Uses latest technology with asynchronous tasks to perform fast and fluid encryption and decryption
– Can use also Blowfish decryption for previous old archive compatibility
– Provides an embedded PDF manual
– Optimized for macOS 10.13 High Sierra
Information
Download AutoCrypt for macOS Free Cracked
Download